Shared Responsibility Model
Security & compliance of an app built in Dittofi is a shared responsibility between Amazon Web Services (AWS), Dittofi & the Dittofi end customer or app developer. This shared model can help to alleviate some of the operational load from the Dittofi client application. This is because AWS operates, manages and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates. Meanwhile, Dittofi assumes responsibility and management of the operating system (including updates & security patches), as well as the configuration of the AWS provided security group firewall. The Dittofi end customer is then only responsible for the authentication & access management to their end Dittofi application.
As shown in the chart, this differentiation of responsibility is referred to in three parts as:
- The security “of” the cloud vs the security “in” the cloud
- The security of the end app i.e. how the app is architected & developed
- The security “in” the Dittofi platform
AWS responsibility “Security of the Cloud” – AWS is responsible for protecting the infrastructure that runs all of the services offered in the AWS Cloud. This infrastructure is composed of the hardware, software, networking, and facilities that run AWS Cloud services.
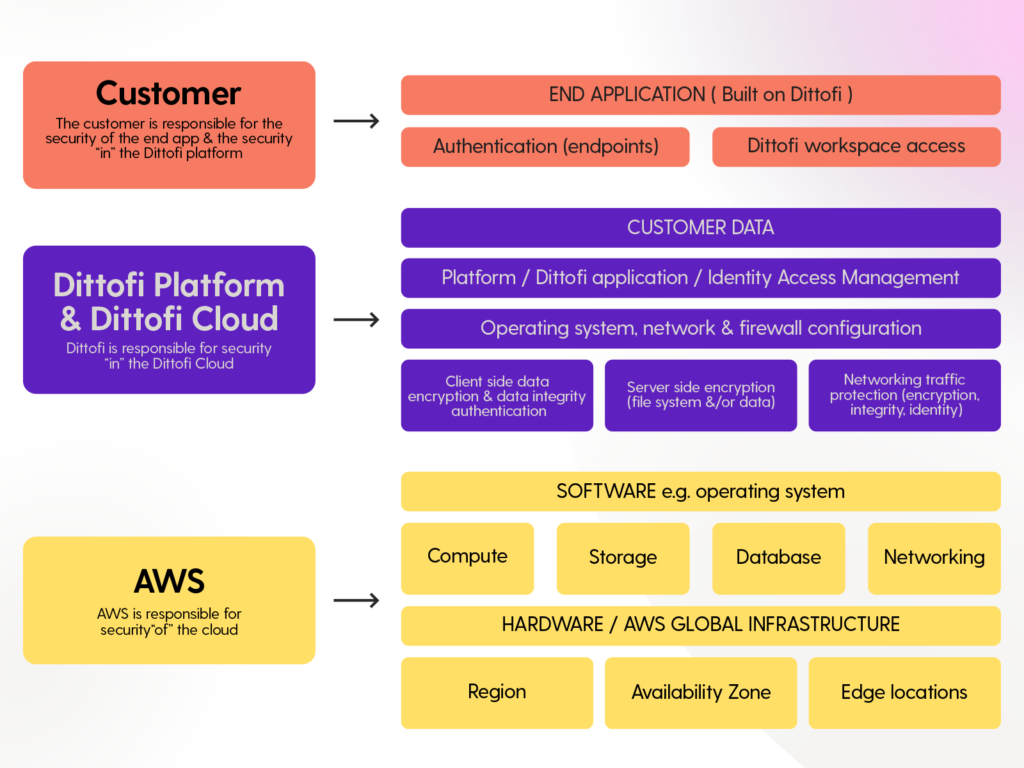
Dittofi responsibility “Security in the Dittofi Cloud” – Dittofi’s responsibility is determined by the choice of AWS services & the configuration of those services used to host Dittofi client apps. Collectively the chosen services & their configuration are known as the “Dittofi Cloud”.
Dittofi DevOps works on the basis that “no matter how good Dittofi DevOps is, AWS knows better”. As such, the list of services selected to run all apps on Dittofi are fully managed AWS services. This means that AWS takes the maximum responsibility by operating the infrastructure layer, the operating system, and platforms, as well as access to the endpoints that store and retrieve Dittofi client data. Each of these services has been setup by Dittofi to ensure that the services are configured according to AWS security best practices.
In this model, Dittofi is responsible for managing client data (including encryption options) & to use IAM (Identity Access Management) tools to apply appropriate permissions on the services that store client data.*
The Dittofi customer also has the option to run the entire Dittofi Cloud inside their own AWS account. This can be achieved with the use of Dittofi ADS (Automated DevOps Solution). In the case where the client runs the services inside of their own account the customer is responsible for the management of their own data (including encryption options) & IAM permissions. This is a zero trust model where Dittofi has only one way access to customer AWS accounts via the AWS APIs.
The customer responsibility “Security of the client app” – The customer is responsible for application level security & access management to their application. This includes ensuring that the Dittofi app is utilised to correctly build password protected endpoints, processes confidential data on the backend of the system, not to take sensitive information outside of PCI systems & so on.
Dittofi helps customers build secure apps by enabling options to use advanced algorithms such for endpoint authentication e.g. bcrypt, providing options to store sensitive information such as passwords with pre configured data types, to securely integrate with PCI compliant systems e.g. Stripe using Dittofi Web Services technology & by automatically performing code quality checks before releasing code into production.
** Please note **
Dittofi conducted a security audit of the Dittofi Cloud which was carried out in March 2023 by AWS partner agency GoForesight. The audit passed their AWS Well-Architected Review.